How Vulnerable Is Your Business to Evolving Cyber Threats?
Stratify IT specializes in crafting tailored, comprehensive cybersecurity solutions for businesses nationwide, encompassing strategic security assessment, multi-layered protection, security governance, and standard operating procedure development.
No matter the scale of your enterprise, safeguarding your organization is paramount. When was your last risk assessment? Are outdated technologies lurking within your systems, leaving you vulnerable to today's sophisticated threats? It's only a matter of time before your defenses are breached.
Relying solely on a firewall or antivirus software is a good initial step, but more is needed. The notion of "set and forget" security settings is tempting yet perilous.
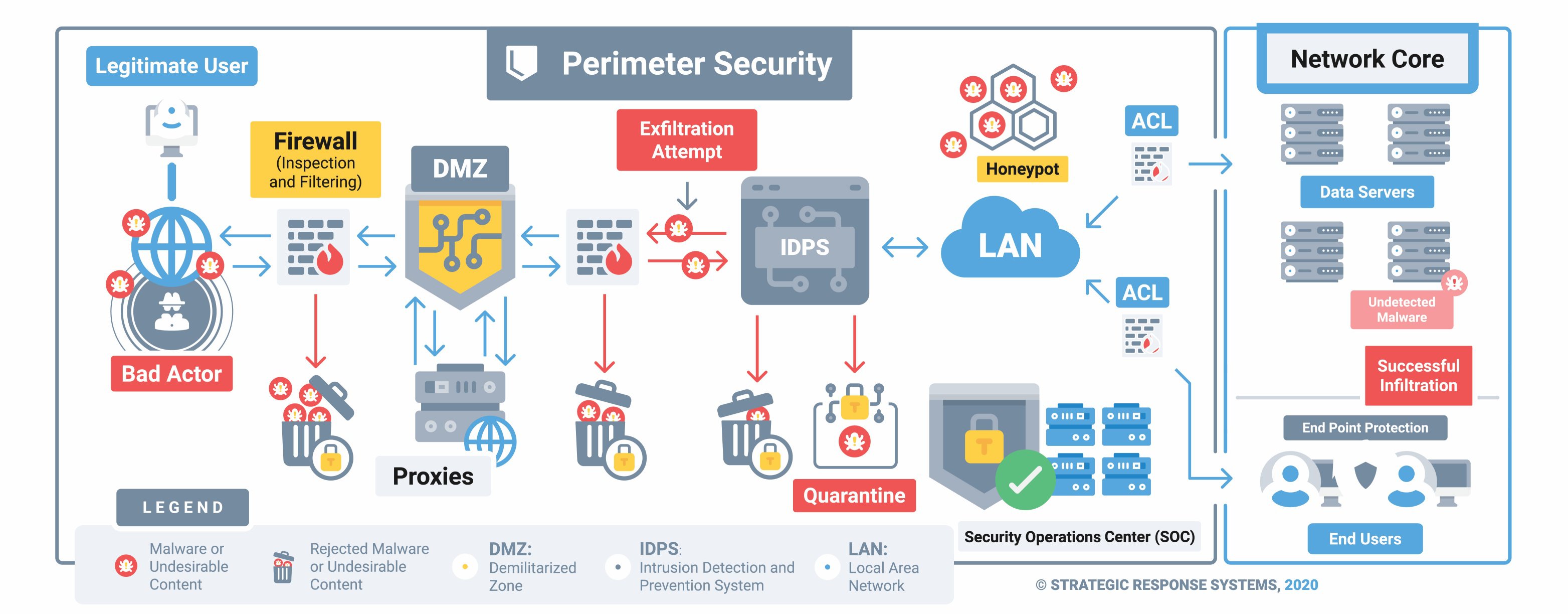
Understanding Modern Cybersecurity Challenges
Given the ever-evolving landscape of cyber threats targeting businesses, securing your IT systems is an ongoing process that demands expert attention and strategic resources. The complexity of these threats requires more than basic protective measures.
Amidst this complexity, there's a clear path forward. Start by fortifying your network perimeter security before addressing internal cybersecurity measures. A multi-layered security approach is essential for modern businesses, and seeking professional cybersecurity guidance is wise. This foundation sets the stage for comprehensive protection that extends beyond traditional security tools.
The Critical Importance of Cyber Insurance Readiness
Building on the foundation of strong cybersecurity measures, cyber insurance has become an essential component of comprehensive business protection. Delaying cyber insurance coverage leaves your business exposed to severe financial consequences that can devastate operations. Insurance providers now scrutinize policyholders' cybersecurity readiness, requiring documented evidence of robust security measures to minimize their risks.
The optimal time to invest in cyber insurance is before a breach occurs. Waiting until after an incident incurs hefty recovery costs and jeopardizes your ability to secure coverage. This timing is crucial because insurance companies evaluate your security posture as part of their risk assessment process.
Balancing liability and security underscores the importance of a strategic cybersecurity stance. Honesty about your infrastructure's security measures is crucial; misrepresentation could leave you uninsured in the event of a breach. This transparency builds trust with insurers and ensures proper coverage when you need it most.
Stratify IT serves as your partner in navigating these complex challenges. We assess your organization's security needs, ensuring a robust defense strategy without draining your resources. Our expertise, particularly in cybersecurity liability insurance requirements, streamlines the process of finding the right coverage for your business while ensuring you meet all insurer expectations.
Ready to enhance your security posture and improve your insurance readiness? Let's start the conversation about protecting your business comprehensively.
Strategic Security Planning Aligned with Business Goals
Effective cybersecurity goes beyond implementing standard security tools—it requires strategic planning that aligns with your unique business objectives. Strategic cybersecurity planning isn't a one-size-fits-all solution for businesses. It's crucial to align your security measures with your specific business goals and risk tolerance. Here's why strategic security planning matters for long-term success:
Focus on What Matters Most
By understanding your most valuable assets and the threats they face, you can prioritize your security investments and efforts.
Cost-Effective Approach
Strategic security helps you avoid wasting resources on unnecessary security measures.
Improved Decision-Making
A clear understanding of your security posture allows you to make informed decisions about future investments in technology and personnel.
Strategic cybersecurity is an ongoing process that requires continuous security assessment, adaptation, and improvement for businesses. This iterative approach ensures your security measures evolve with both your business growth and the changing threat landscape.
By taking a strategic approach to cybersecurity, you can build a strong defense against cyber threats and ensure the long-term success of your organization in today's competitive business environment. This foundation of strategic thinking sets the stage for realizing the full benefits of comprehensive security planning.
Measurable Benefits of Strategic Security Implementation
Understanding the strategic approach to cybersecurity naturally leads to examining its concrete benefits for your organization. Cyber threats are a constant concern for businesses, and implementing a strategic security approach offers a multitude of advantages that go far beyond simply preventing cyberattacks. These benefits create lasting value for your organization and stakeholders.
Some key benefits you can expect when adopting a comprehensive strategic security posture:
Reduced Risk of Cyberattacks and Data Breaches
Strategic security goes beyond reactive measures. It involves proactive identification and mitigation of vulnerabilities in your IT infrastructure and security protocols. This proactive approach significantly reduces the likelihood of successful cyberattacks and data breaches, protecting your valuable information and assets.
Improved Compliance with Industry Regulations
Many industries have stringent data privacy and security regulations. Strategic security ensures your organization adheres to these regulations by implementing the necessary controls and procedures. This not only avoids potential hefty fines but also demonstrates your commitment to data protection, fostering trust with regulators and stakeholders.
Enhanced Business Continuity and Resilience
Cyberattacks can disrupt your daily operations and cause significant downtime, leading to lost revenue and productivity. Strategic security focuses on building resilience against such threats. It includes measures for disaster recovery and business continuity, ensuring your organization can quickly recover and bounce back from security incidents with minimal disruption.
Increased Employee and Customer Confidence
Data breaches and cyberattacks can erode trust in your organization. Strategic security demonstrates your commitment to protecting sensitive data, reassuring both employees and customers that their information is secure. This fosters a more positive work environment and builds stronger customer relationships.
By implementing a strategic security approach, you gain a comprehensive defense against cyber threats, ensure regulatory compliance, and ultimately empower your business for long-term success.
Stratify IT: Building a Secure Future for Your Business
We understand cybersecurity's critical role in today's digital landscape. That's why we offer comprehensive security solutions to safeguard your organization's data and systems.
Our Strategic Security Approach
Security Assessments
We thoroughly examine your IT infrastructure and security posture to identify vulnerabilities and potential weaknesses. This proactive IT assessment approach allows us to address any issues before cybercriminals can exploit them.
Security Planning
After analyzing your specific needs and goals, we collaborate with you to craft a customized strategic security plan. This plan will serve as a roadmap for implementing robust security measures that align seamlessly with your business objectives.
Security Implementation
We will then implement industry-leading security controls, including firewalls, intrusion detection systems, and access management solutions. These solutions work together to create a multi-layered defense against cyber threats.
Managed Security Services
We don't stop at implementation. Our ongoing Managed Security Services provide 24/7 monitoring and management of your security environment by our security professionals. This proactive approach ensures that your defenses remain vigilant and that potential threats are identified and addressed swiftly.
Cybersecurity Awareness Training
Empowering your employees is vital in the fight against cybercrime. We offer comprehensive Cybersecurity Awareness Training programs that educate your staff on recognizing and avoiding cyber threats, further strengthening your overall security posture.
Cloud Security Solutions
As cloud adoption grows, securing your data and applications in the cloud environment is paramount. Our cloud security solutions are designed to protect your valuable assets in the cloud while ensuring optimal performance and scalability.
HIPAA and CMMC Compliance
Navigating complex industry regulations can be challenging for organizations in healthcare (HIPAA) or the defense industrial base (CMMC). We offer expert guidance and support to ensure compliance with these critical regulations.
By partnering with Stratify IT, you gain a trusted security advisor with the expertise and experience to safeguard your organization's digital assets. Let us help you build a secure future for your business.
Why Choose Stratify IT for Strategic Security?
Safeguarding your organization's data and systems is no longer an option, it's a necessity. Here at Stratify IT, we offer a powerful combination of experience, expertise, and a proven approach to secure your business.
Why Partner with Stratify IT?
Unparalleled Experience
For over 20 years, we've been at the forefront of cybersecurity, protecting businesses of all sizes from evolving cyber threats.
Trusted Expertise
Our team comprises highly certified cybersecurity professionals with in-depth knowledge and a proven track record of delivering comprehensive cybersecurity solutions.
Strategic Approach
We go beyond technical controls. Our approach addresses the technical aspects of your cybersecurity posture and the human element through user security awareness training.
Prioritizing Your Privacy
Your privacy and confidentiality are paramount to us. We adhere to the highest standards to ensure your information is secure and treated with the utmost discretion.
Easy Consultation Process
If you're looking to strengthen your organization's cybersecurity, we invite you to explore our comprehensive cybersecurity audit checklist. This valuable resource outlines key steps to identify vulnerabilities and enhance your security posture. Additionally, our team offers tailored cybersecurity solutions designed to protect your business from potential threats. Visit our checklist and learn more about how our services can help safeguard your sensitive data. Contact us today to schedule a consultation. We'll discuss your needs, outline our approach, and get started on delivering the results.
What Makes Stratify IT Reliable and Trustworthy?
We prioritize reliability and integrity in every facet of our work. Our team approaches each assignment with a dedicated and conscientious mindset, ensuring we maintain the highest standards.
Commitment to Trustworthiness
We understand that security is not just about physical protection—it's about fostering peace of mind. That's why we collaborate closely with our clients, ensuring clear communication and unwavering support at every step.
Integrity at Every Turn
Our commitment to integrity means that you can count on us to be transparent and dependable in all our interactions. We don't just promise reliability; we deliver it consistently, ensuring your security needs are met with the utmost care and professionalism.
Choose Stratify IT for a trusted cybersecurity partner backed by a steadfast commitment to reliability and integrity.
How does Stratify IT deliver comprehensive cybersecurity solutions to protect your business from evolving threats?
Stratify IT designs a strategic action plan that includes Assessment, Protection, Governance, and SOP Development for each client's unique needs. From deploying cutting-edge technologies that ensure real-time communication and updates to staying ahead of legislative changes and adjusting strategies accordingly, we are committed to maintaining a high standard of cybersecurity readiness.
Comprehensive Security Solutions
Real-time Updates
Leveraging advanced technology, we keep our clients informed with immediate updates about their security status, helping them stay proactive rather than reactive.
Legislative Compliance
Our governance services are continuously updated to reflect the latest legal requirements, ensuring that your operations are always compliant with current laws.
Customized Strategies
Recognizing the diversity of security challenges, we meticulously develop Standard Operating Procedures (SOPs) that are not only robust but also flexible enough to adapt to unforeseen circumstances.
This strategic approach allows us to provide a reliable and effective service that not only meets but exceeds the expectations of our clients, ensuring all-around security preparedness regardless of the situation. By integrating these detailed practices into our holistic security solutions, Stratify IT stands as a pillar of unwavering support and expert reliability in the ever-evolving landscape of security threats.
Cybersecurity and Cyber Insurance: A Powerful Partnership
A strong security posture is not only essential for protecting your valuable assets but it can also play a significant role in your ability to obtain cyber insurance and potentially qualify for better rates.
Cyber Insurance Explained
Cyber insurance is a financial safety net that helps businesses recover from losses incurred due to cyberattacks, such as data breaches, business interruptions, and cyber extortion.
The Connection
Cyber insurance providers assess an organization's risk profile before issuing a policy and determining the premium. By implementing a strategic security plan that demonstrably strengthens your security posture, you can significantly reduce your risk profile, making you a more attractive candidate for cyber insurance and potentially lowering your premiums.
Ready to Take Control of Your Security?
Let Stratify IT be your trusted partner in building a robust and strategic security plan.
Get a Free Security Assessment
Identify your vulnerabilities and gain valuable insights into your current security posture. Get a Free Security Assessment
Schedule a Consultation
Discuss your specific needs and explore how our customized solutions can secure your business. Schedule a Consultation
Download a Whitepaper on Strategic Security Planning
Learn the essential elements of crafting a successful security plan. Download a Whitepaper on Strategic Security Planning
Don't wait until it's too late. Take action today and ensure a more secure future for your business.
Stratify IT does not sell cyber insurance, but we can help you understand the benefits and guide you toward reputable insurance providers.
Discover how our cybersecurity solutions safeguard businesses from threats. Explore our leadership blogs for expert insights and best practices in cybersecurity.
Ready to Get Started?
Let's discuss how our strategic security solutions can protect your business and prepare you for cyber insurance
